Having a plan, or not, to secure your enterprise and respond to an incident could be the difference between closing down your company or seeing that incident through!
Most large organisations invest considerable amount of time, money and resources to define a Cyber Security Strategy resulting in several Cyber Security Programs and Incident Management/Response Plans.
All of which are in support of a wider Business Continuity Plan (BCP).
This results in procedures, documentation, backup systems, regular incident simulations and dedicated teams.
As long as these initiatives are kept up to date and still relevant to the organisation mode of operation then it should help a company survive most incidents.
By contrast, smaller organisations and especially start-ups tend to focus first on getting the "job done" and then think of what to do in case of an emergency or incident.
Their Cyber Security Programs and Incidence Response Plans are often limited to the delegation of the IT overhead to 3rd parties and rely on their availability, integrity and performance guarantees.
This does not prepare such companies to face most emergencies or incidents as the IT infrastructure is only part of what could go wrong.
Defining a Cyber Security Program and Incident Response Plan does not have to be complex, time consuming and costly. More importantly, it shouldn't be delayed and left as the last thing to do.
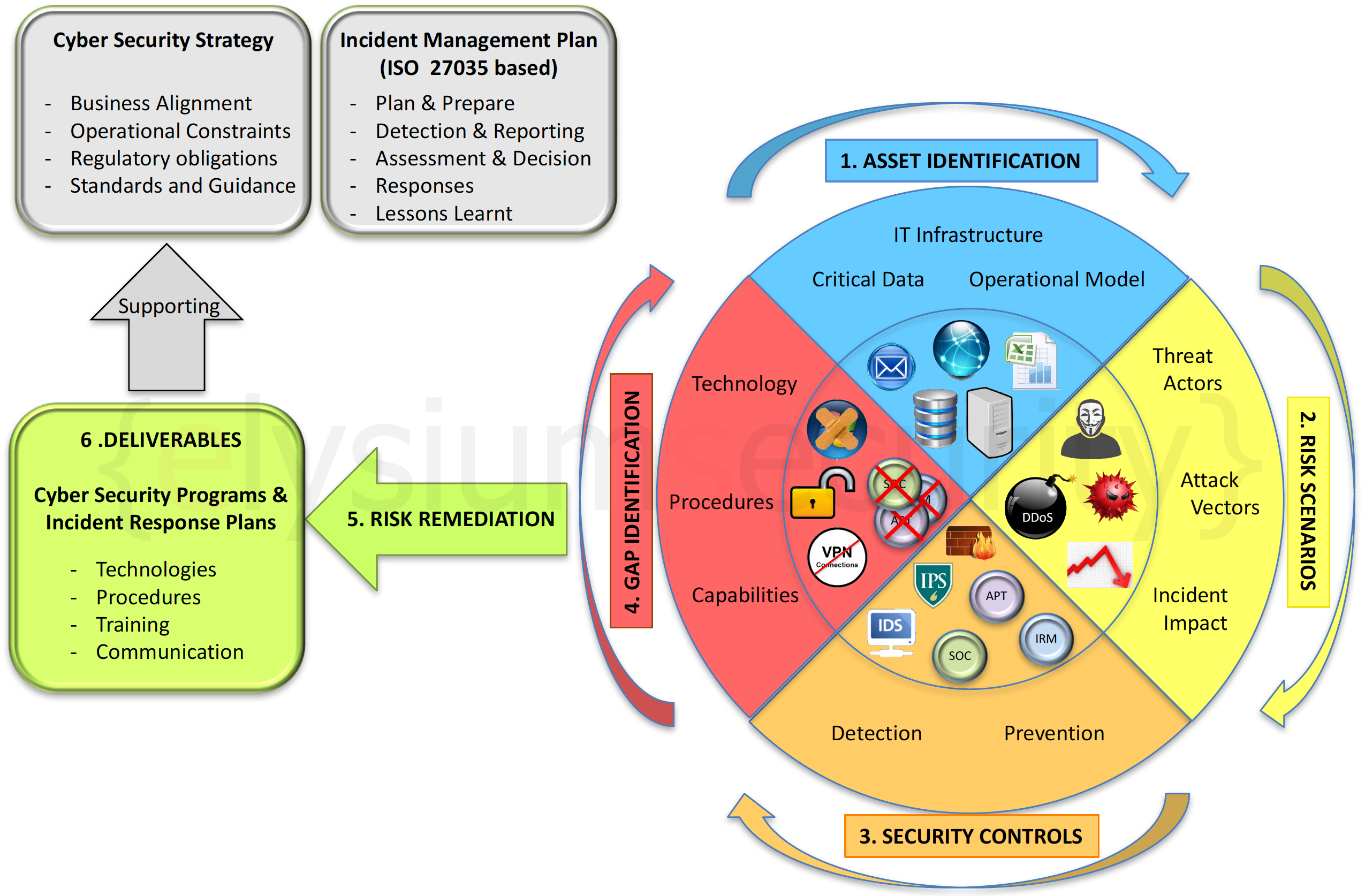
ElysiumSecurity has designed a simple 6 steps methodology aimed at defining a Cyber Security Program and Incident Response Plan in support of a Cyber Security Strategy and Incident Management Plan. It is simple, fast, focused and practical.
More importantly, anyone can use it to kick start their Incident Response initiative!
The methodology follows a 6 steps lifecycle, described in the diagram below, and answers 6 core questions:
- ASSET IDENTIFICATION: What do you have? Identify the customer IT environment, operating model and what asset/data is critical to the organization;
- RISK SCENARIOS: What do you fear? From the answers gathered in the previous step, core risks and realistic attack scenarios will be defined to understand what the customer must protect;
- SECURITY CONTROLS: What are you doing about it? Review the existing security controls and procedures in place to detect and prevent cyber incidents;
- GAP IDENTIFICATION: What are your security gaps? Identify the IT Security gaps by reviewing the attack scenarios identified in the second step against the existing security controls in place;
- RISK REMEDIATION: What cyber risks you want to remediate? Agree the risk remediation required by the customer to protect their business through technology selection, procedure documentation and capability training/enrolment;
- DELIVERABLE: What you need to do next? Produce a bespoke and relevant Cyber Security Program and Incident Response Plan to implement the agreed risk remediation steps described above.
i.e.: IT Infrastructure, Critical Data, Operational Model
i.e.: Loss of competitive advantage, data leakage, denial of service
i.e.: Current Security controls: IDS, Firewall, Web Filtering, A/V
i.e.: Lack of Security Operation Center, IPS, Information Right Management
i.e.: Detect Intrusion through SOC, Prevent data leakage through Encryption
I.e.: Open Source and commercial Technologies available, procedures creation

 RSS Feeds
RSS Feeds Cyber Security Planning - A simple 6 Steps Approach
Cyber Security Planning - A simple 6 Steps Approach