Note: This is the first post of a two parts series on how to use IDS in a different way.
Intrusion Detection Systems such as Snort and Suricata
are traditionally seen as Defensive tools, and in essence they are. They can alert on security issues occurring on your network such as Botnet Activities, network based attacks, hosts/servers activities and vulnerabilities.
That last point is important.
It is important because that same information used for defence activities, could be used by an attacker as part of an attack reconnaissance. For example, being able to identify a list of hosts that use outdated SSH/SSL servers, a vulnerable Flash Client or other vulnerable software/services; HTTP logs highlighting users web activities, clear text passwords, etc.
When looking at an IDS that way, it becomes a passi...
>>[READ MORE]
{elysiumsecurity} 
Cyber Protection & Response
Security News (111 Posts)
 IDS used as an Offensive Security Tool
IDS used as an Offensive Security Tool
 Securing your Cloud Storage with a Boxcryptor alternative called EncFS
Securing your Cloud Storage with a Boxcryptor alternative called EncFS
Cloud storage providers such as Dropbox, Box, One Drive, etc. are increasingly being used for both personal and business reasons. On the Business side, often without the individual's company fully aware of what data is actually leaving their premises.
One of the issue with storing data in the cloud is Security. Looking at Dropbox in recent years, there has been a number of embarrassing blunders which resulted in their customers' data becoming available to anyone who knew where to look. We did blog about it several times: here, here and here. Many other security blogs also related those stories, such as this nice summary from Sophos.
To limit the risks relat...
>>[READ MORE]
 How to reduce WEB 2.0 attack surface by going back to WEB 1.0, the dynamic way!
How to reduce WEB 2.0 attack surface by going back to WEB 1.0, the dynamic way!
The arrival of WEB 2.0 brought dynamic content through the use of technologies such as Java, Flash and PHP.
Consequently it also widen the attack surface. Websites became prettier, more interactive, easier to update and also easier to attack!
The need for further functionality was, as it is often the case, at the cost of security.
The four diagrams below illustrates the differences between a WEB 1.0 and a WEB 2.0 architecture as well as highlighting the increased attack surface.
In a typical WEB 1.0 architecture, besides the physical, human and network security considerations, protecting the data is dependant of the Operating System and the application security layers. Typically, the application security layer is restricted to the Web Server (i.e.: Apache) if no other services/applications are exposed to the Internet.
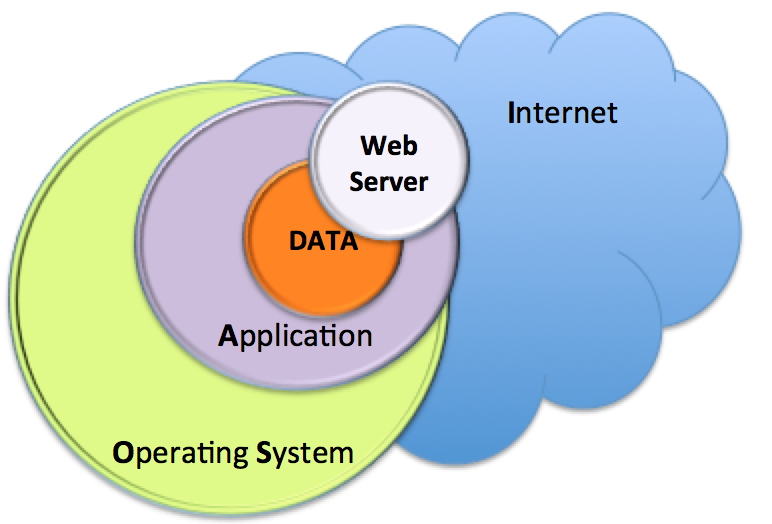
Diagram 1 - WEB 1.0 Typical Ar...
>>[READ MORE]
 SELKS 2.0 vs. Security Onion
SELKS 2.0 vs. Security Onion
I have recently been testing SELKS v2.0 which is an open source Network Security Monitor (NSM) based on an
ELK framework: Elasticsearch (search and analytics engine) Logstash (log normalisation) Kibana (visualisation).
The NSM core engine is provided by the first "S" which stands for Suricata (Network IDS) and the last "S" which stands for Scirius (Management GUI for Suricata).
SELKS is provided as a live Linux distribution based on Debian 8 (Jessie) which is also installable.
SELKS V2.0 is a great improvement from SELKS V1.0, so much so that I now consider it a serious contender to Security Onion (SO) at...
>>[READ MORE]
 BlackHat Mobile Security Summit - London 2015
BlackHat Mobile Security Summit - London 2015
In June 2015 I attended the Blackhat Mobile Security Summit in London, a 2 days event filled with talks from various researchers and security professionals, there was a 3rd day in the form of a workshop for anyone attending the Interop London hosting event
Blackhat is historically a USA based event with its main conference taking place in Las Vegas every year, lately they started to host similar (but smaller) conferences around the world such as in Singapore and Amsterdam (which I blogged about last year here).
This London edition was definitely on the "smaller" side and this actually had a few advantages:
The quali...
>>[READ MORE]
 Hackfu2015 Challenge 7 - Solution
Hackfu2015 Challenge 7 - Solution
This is part of my write up from the Hackfu 2015 Security Challenge.
The third and last challenge I solved was surprisingly very easy, but there might have been more to it...
The instructions given were:
Below is how I solved that challenge:
We first run the following command to see all the printable/ASCII strings from the binary.
> strings shipbinary
Below is an extract of the most interesting result from the above command.
Enter Decryption Code:
burnthelandandboilthesea
Code Accepted.
Establishing Connection to Planet Abaddon...
out.txt
123.123.123.1 -c 1 | tail -1| awk '{print $4}' | cut -d '/' -f 2
>>[READ MORE]
 Hackfu2015 Challenge 5 - Solution
Hackfu2015 Challenge 5 - Solution
This is part of my write up from the Hackfu 2015 Security Challenge..
The second challenge I solved was in fact quite easy because I solved a similar one for the SANS Summer challenge in 2014 (where it took me much longer to solve the first time I came across this type of steganography!)
The instructions given were:
Below is how I solved that challenge:
But, If you load the file in a windows software such as Sonic Visualizer, add a layer to show a Spectrogram ...
>>[READ MORE]
 Hackfu Challenge 2015 - Solution for Challenge 1
Hackfu Challenge 2015 - Solution for Challenge 1
MWR ran a Security Challenge last April, unfortunately I only found out about it 3 days before the dead line! I still managed to solve 3 out of the 7 challenges and really enjoyed them.
The first challenge was especially interesting, as I like cryptography. This was a tough one!!!
The instructions given were
That's pretty much it! Below is how I solve this challenge and cracked the code:
I used information on PocketRC4 f...
>>[READ MORE]
 One more update to the Security Onion Guide
One more update to the Security Onion Guide
We have updated once more our Security Onion Installation Guide with a few tweaks regarding setting up BRO emails and SSH.
There is also a new PDF version, using an updated template, available from the download section .
>>[READ MORE]
 Updated Security Onion Guide
Updated Security Onion Guide
Last week, Security Onion repository moved from Google Code to Github. We have now updated our Security Onion Installation Guide with the new links.
Basically, replacing the base part of each link from the old reference
"https://code.google.com/p/rest_of_the_link]"
to
"https://github.com/Security-Onion-Solutions/rest_of_the_link]"
If you are looking for "issues", not only do you need to replace the base reference as mentioned above, but you also need to remove the "detail?id=" at the end of the URL.
For example:
https://code.google.com/p/security-onion/issues/detail?id=488 (does not work )
Becomes
https://github.com/Security-Onion-Solutions/security-onion/issues/48...
>>[READ MORE]
 RSS Feeds
RSS Feeds