ElysiumSecurity was invited by the Mauritian National Computer Security Incident Response Team (CERT-MU) to present at the FIRST Technical Colloquium 2017 which took place on the 30th of November 2017.
We gave a presentation on how IDS can be used both as a traditional defensive tool and also a more original offensive tool.
The aim of this presentation was to introduce the attendees of the various free and Open Source IDS offerings and to highlight the benefits and key components of a successful IDS implementation.
It was also emphasised on how easy it is to get started with an IDS both from a software and hardware point of view.
Below is a link to our presentation. If you want a more complete narrative please fee free to contact us for more information.
We would like to thanks the Mauritian National Computer Board ...
>>[READ MORE]
{elysiumsecurity} 
Cyber Protection & Response
Security News (111 Posts)
 FIRST Technical Colloquium 2017 in Mauritius - Our presentation on IDS
FIRST Technical Colloquium 2017 in Mauritius - Our presentation on IDS
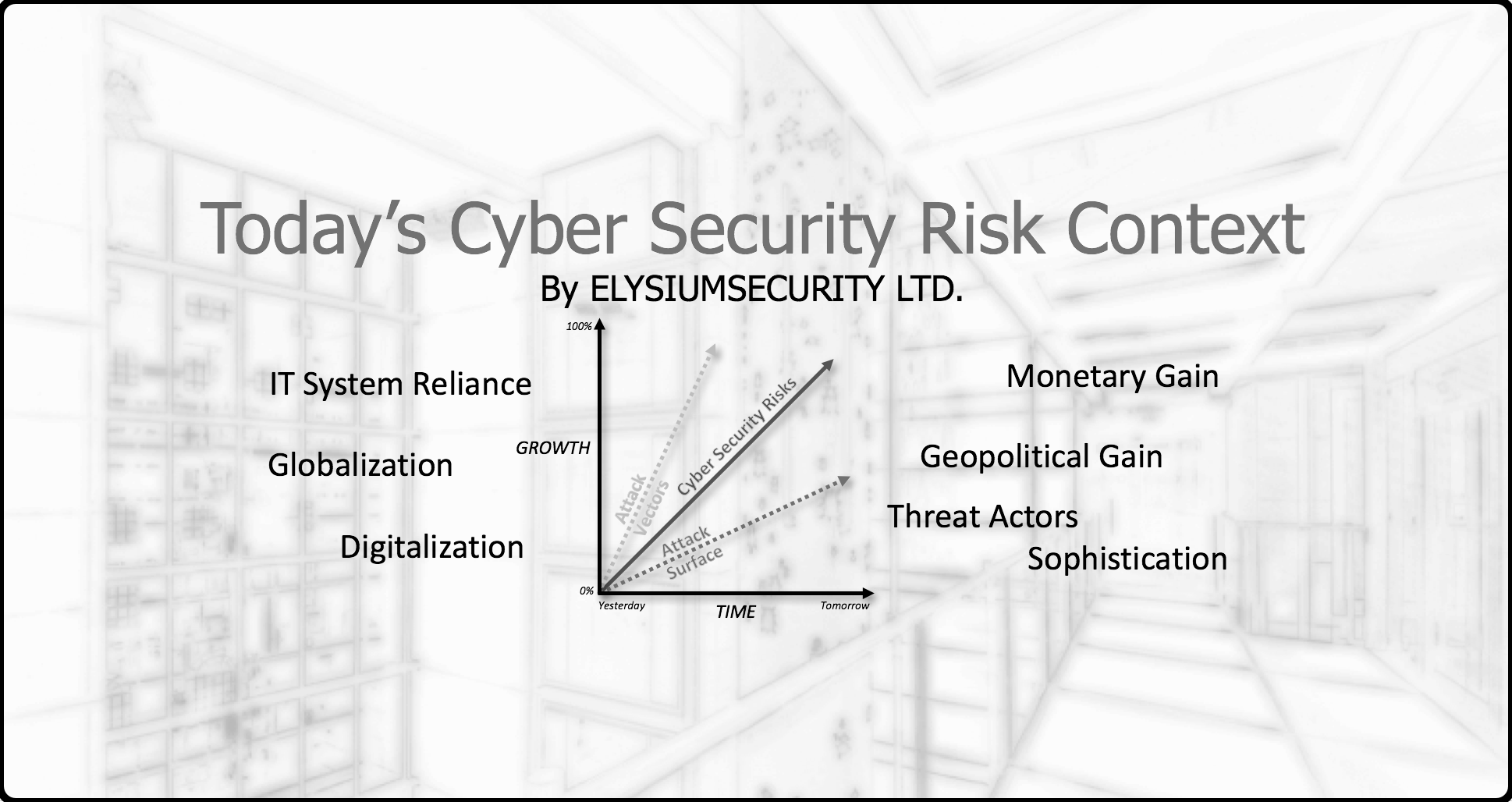 Today's Cyber Security Risk Context
Today's Cyber Security Risk Context
In an attempt to make a wordy presentation slide into something more palatable,
I created this infographic to illustrate the main contributing factors of the growing attack surface and attack vectors faced by many organisations today.
This contributes to an overall growth of their Cyber Security Risks posture.
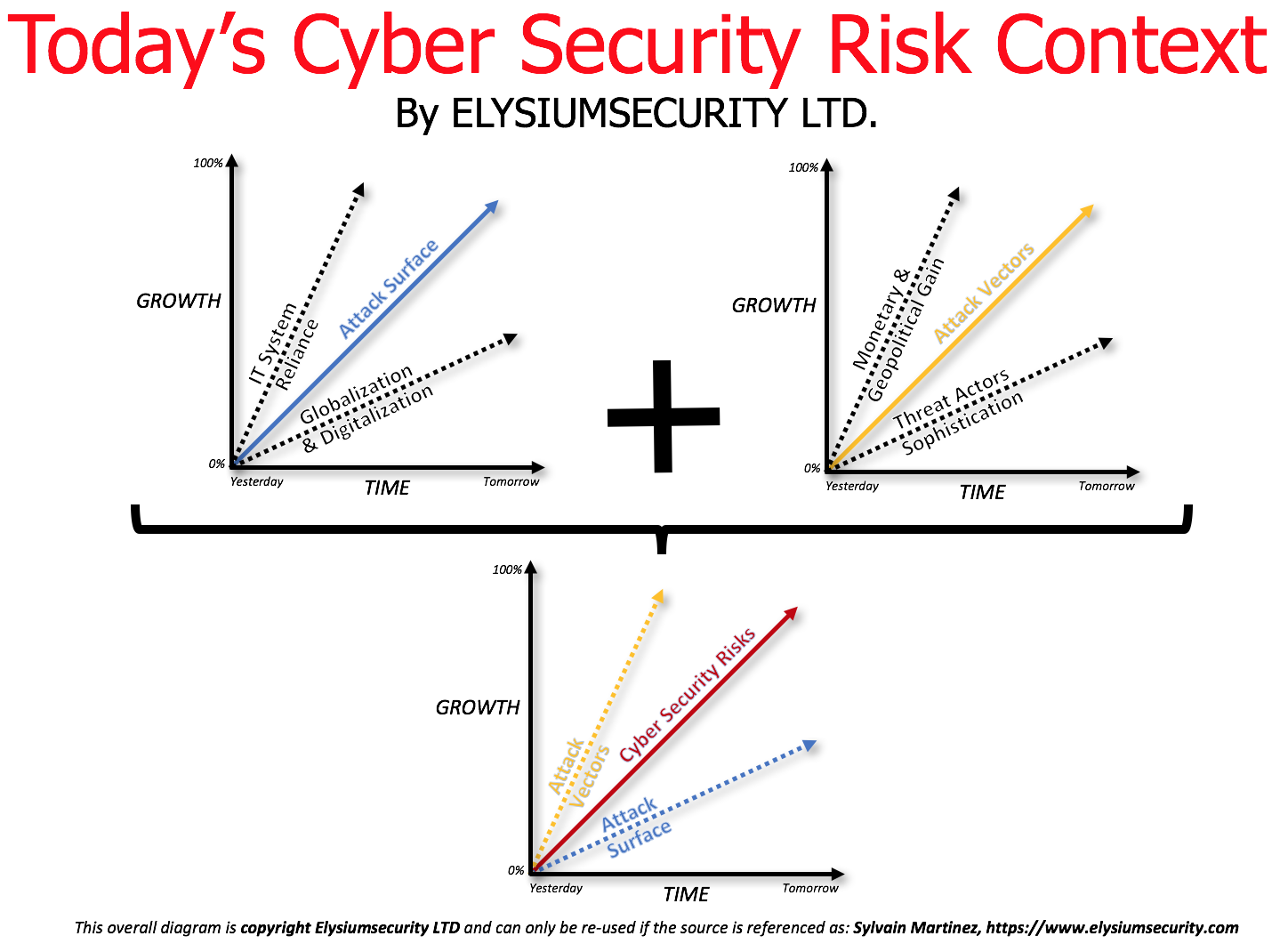
ElysiumSecurity Ltd can help your organisation with assessing its attack surface and attack vectors to better understand its overall Cyber Security Risk posture and the remediation steps that should be prioritised.
Contact us today for a free consultation at: [email protected]
...
>>[READ MORE]
 GDPR and what it means to companies in the Indian Ocean and Africa
GDPR and what it means to companies in the Indian Ocean and Africa
With fines for non-compliance of up to 4% of a company’s annual global turnover or €20 Million (whichever is greater), and applicable regardless of the company’s location (i.e.: Mauritius). GDPR is a regulation that can no longer be ignored from any companies processing personal data of EU Residents (i.e.: travel agencies, hospitality, banking, health care, insurance, etc.).
This article provides key facts as well as some resources to get started on the road to GDPR compliance.
---
1. Key facts about GDPR;
2. Relevant Definitions;
3. The route to GDPR compliance;
4. Going further.
---
1 - Key facts about GDPR
>>[READ MORE]
 Are Cyber Security Challenges and Opportunities in Mauritius and Africa different from Europe?
Are Cyber Security Challenges and Opportunities in Mauritius and Africa different from Europe?
Spoiler alert: the answer to this question is "not really". However, the subtle differences that do exist are important to acknowledge in order to successfully implement or provide Cyber Security in those locations.
I was interviewed recently for an upcoming article about Cyber Security in a regional African and Indian Ocean magazine called Eco Austral. As I answered the journalist's questions I wondered how different those answers would be if it was for a European magazine.
In this blog article, I will first provide the answers to the four questions I was asked in the wake of recent Ransomware attacks that generated a lot of public attention. I will then expand on those questions and will be looking at the different Cyber Security contexts for those regions in terms of advantages and disadvantages to, finally, identify common opportunities and challenges.
PART 1 - CYBER SECURITY...
>>[READ MORE]
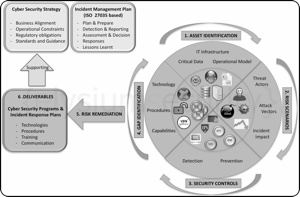 Cyber Security Planning - A simple 6 Steps Approach
Cyber Security Planning - A simple 6 Steps Approach
Having a plan, or not, to secure your enterprise and respond to an incident could be the difference between closing down your company or seeing that incident through!
Most large organisations invest considerable amount of time, money and resources to define a Cyber Security Strategy resulting in several Cyber Security Programs and Incident Management/Response Plans.
All of which are in support of a wider Business Continuity Plan (BCP).
This results in procedures, documentation, backup systems, regular incident simulations and dedicated teams.
As long as these initiatives are kept up to date and still relevant to the organisation mode of operation then it should help a company survive most incidents.
By contrast, smaller organisations and especially start-ups tend to focus first on getting the "job done" and then think of what to do in case of an emergency or incident.
Their Cyber Security Programs and Incidence Response Plans are often limited to t...
>>[READ MORE]
 The 2015 SANS Holiday Hack Challenge Write-Up
The 2015 SANS Holiday Hack Challenge Write-Up
For the last 12 years, SANS/Counterhack offers a hacking challenge over the Christmas period. It is a great event, fun and with an increasing level of difficulty which lets everyone having a go.
This year, The 2015 SANS Holiday Hack Challenge was built around a great 8-bit retro web gaming platform where you had to run around a virtual town to find the various hacking challenges.
The plot was centered around a fictitious toy, a gnome, that everyone wanted to have in their home for Christmas. However, two kids found the toy was "behaving" strangely and something was going on.
Through the challenge you will learn that the gnomes had in fact a hidden built-in camera and were transmitting photos to 5 super gnomes (servers) by connecting to free surrounding WIFI netwo...
>>[READ MORE]
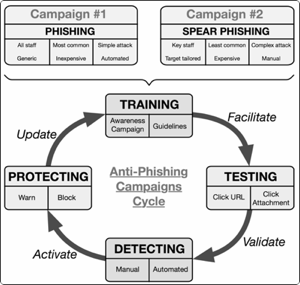 How to build an efficient Anti-Phishing Framework?
How to build an efficient Anti-Phishing Framework?
As our world reliance on electronic connection and communication is accelerating, cyber attacks are on the rise along with
counter measure solutions in the form of endless new cyber security companies, consultants, expertise, software and hardware
aimed at protecting individuals, assets, corporations and even nation states.
However, even with all the tools and increasing cyber budget at our disposal, there is always one constant weak link:
The Human element in the so called Cyber Kill Chain.
It is this human element that can defeat the most sophisticated defence systems and it is why the use of Phishing and
Spear Phishing attacks are so prominent and successful.
Those attacks exploit human emotion, ignorance and credibility to bypass defences in tricking users to follow poisonous steps:
Clicking on links, opening documents, accepting/ignoring security warnings and good practises, installing software, etc....
>>[READ MORE]
 How to build a Red Team and Why?
How to build a Red Team and Why?
I recently gave a talk at the Rant Forum in London on the topic of
"RedTeam, why this is more than a buzz word?".
It was an interesting experience and whilst different from traditional security events, as the crowd can and will interrupt you at any time, it was very enjoyable.
Many attendees asked if I could produce some "slides" after the talk. As no slides were used, below is a collection of notes from wich the talk was based on.
In this post we will explain what RedTeam is, how does it fit with other similar security services and what advantages does it bring to an organisation.
We will also look into what works? what doesn’t? And where is this “new” type of service going?
1. DEFINITION
A Red Team is part of a trio of services which increases in sophistication: Vulnerability Assessment, Penetration Testing and then Red Teaming.
We will d...
>>[READ MORE]
 RANT FORUM - Red Team Recipes Presentation
RANT FORUM - Red Team Recipes Presentation
I will be giving a talk tomorrow evening, the 28th of November at around 6pm, in London at the Risk and Network Threat (RANT) Forum .
The topic is:
Why RedTeam is more than just a buzz word? What works? What doesn't? And where is this "new" type of service might be going? All those questions answered by someone who is actually delivering Red Team activities.
Registration is free, you get free drinks and food... plus you get to hear me talk, so what is not to like?! :)
You can register HERE
The RANT Forum is quite different from your typical free security briefing, for a start it is not a sales forum. However, the company behind it is a recruitment agency, so they are still interested in taping the UK Security professional community!
...
>>[READ MORE]
 IDS used as a Network Forensic Tool
IDS used as a Network Forensic Tool
Note: This is the second post of a two parts series on how to use IDS in a different way.
Intrusion Detection Systems are traditionally seen as Defensive tools. They can however be used for different purposes than initially designed for as highlighted in the previous post , where we discussed how IDS could be used as an offensive tool.
The popularity of pre-configured/packaged IDS environments such as SELKS or Security Onion provide various software packages and Graphical User Interfaces to navigate through large volume of data by parsing/categorising/filtering it automatically.
More importantly, such systems are starting to provide mo...
>>[READ MORE]
 RSS Feeds
RSS Feeds