When it comes to password expiry, different companies have different policies.
Whilst the current industry standard is 90 days, a lot of companies do enforce a lower 30 days period or anything in between 30 and 90 days.
If you ask the users, they do not tend to be happy with changing passwords often and even at all (are you?)
The problem with changing passwords often is that, unless you are using some kind of password safe with random generated passwords, users tend to just change a letter or number at the end of their password (1, 2, 3 or 2019, 2020, etc.), chose another weak password all together or write it down somewhere.
And if users do that, then changing their passwords often does not improve your security posture.
We therefore advise not to go lower than 90 days when it comes to password expiry, in fact when it comes to authentication security, we would highly recommend that you enforce dual factor authentication through SMS or App for s...
>>[READ MORE]
{elysiumsecurity} 
Cyber Protection & Response
Security News (111 Posts)
 The problem with password expiry
The problem with password expiry
 Afer 17 years, a NEW BUGS Cryptography Package for Unix (version 4.1.2)
Afer 17 years, a NEW BUGS Cryptography Package for Unix (version 4.1.2)
BUGS is a personal cyber security project from Sylvain Martinez, which started about 25 years ago and has enabled him to kick start his career in Cyber Security.
As such it has a special place in the heart of ELYSIUMSECURITY.
It is an open source project where Sylvain created his own symmetric cryptography algorithm along with a few applications to showcase the capability of his cryptography algorythm:
An application to encrypt/decrypt files, a simple encrypted chat application, a secure shell add-on, a password manager, etc.
This project is a hobby and should only be seen as that, any respectable professional cryptographer would tell you this: "Do not create your own cryptography algorithm"!
Furthermore, we always advise our clients to only use international standard algorithms (i.e.: AES)
Having said that, it doesn't mean we cannot have a go ourselves!
It had the merit of teaching us a lot about cryptography and after all, no one ha...
>>[READ MORE]
 2019 CYBER SECURITY TRENDS REPORT OVERVIEW
2019 CYBER SECURITY TRENDS REPORT OVERVIEW
In the past 6 months, ELYSIUMSECURITY has looked at 10 of the most popular Cyber Security reports of 2019 and created an overview document summarising their main trends and predictions.
The results will be presented at the next MU.SCL event (free registration HERE) but you can already have a look at the main findings by downloading the presentation in the DOWNLOAD section.
>>[READ MORE]
 PHISHING PROTECTION FRAMEWORK
PHISHING PROTECTION FRAMEWORK
ELYSIUMSECURITY has designed a practical framework to help organisations implement an efficient Phishing Protection program.
Phishing has become the number one attack vector used by criminals to get around most companies defences and use social engineering to extract confidential information and conduct financial frauds.
For an efficient Phishing Protection program, organisations must consider not only implementing awareness and simulation campaigns but also integrate them to their phishing detection and protection strategy.
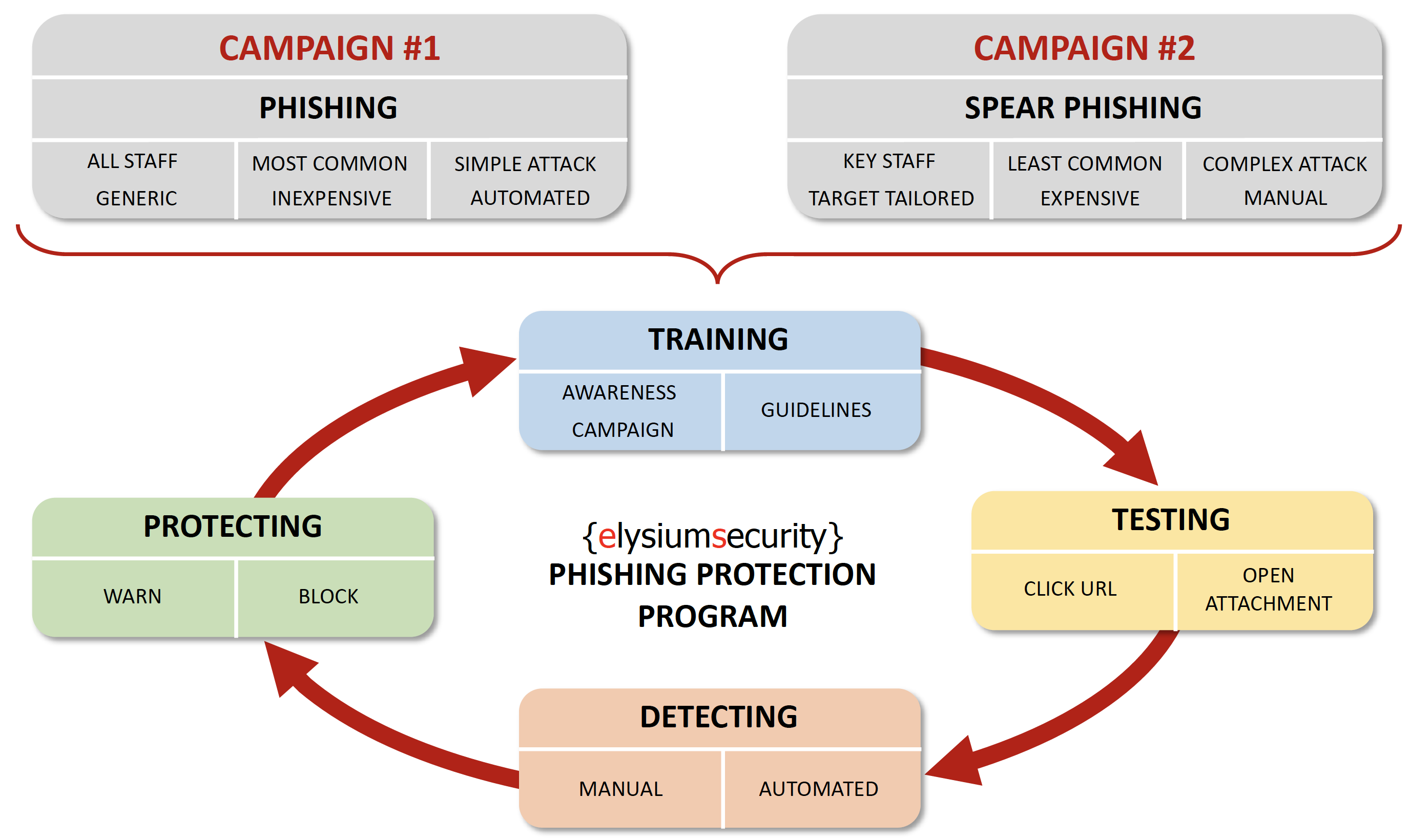
More information on how to implement this framework is available in our DOWNLOAD section.
>>[READ MORE]
 NATIONAL CYBER SECURITY DRILL 2019
NATIONAL CYBER SECURITY DRILL 2019
ELYSIUMSECURITY was asked to participate in the 2019 Mauritius National Cyber Drill
where we presented on Incident Response in front of Mauritian organisations that are critical to the operation of the country.
We took this opportunity to introduce the core concepts of the NIST SP 800-61 Incident Response framework.
We also provided a high level view of the ELYSIUMSECURITY Incident Response framework, which is a practical implementation of the NIST SP 800-61 Incident Response frameworkand the FIRST CSIRT services Framework
The updated presentation slides are available in our DOWNLOAD section...
>>[READ MORE]
 HOW TO CHOOSE MICROSOFT 365 SECURITY PLANS AND ADD-ONS: E3, E5, EMS E3, EMS E5, 365 E3, 365 E5
HOW TO CHOOSE MICROSOFT 365 SECURITY PLANS AND ADD-ONS: E3, E5, EMS E3, EMS E5, 365 E3, 365 E5
Knowing what security features are included or not in the different packages offering from Microsoft can be confusing.
In this article, we will explain the overall principle of what all of those plans means.
For most companies, when it comes to Microsoft products you need protection for your EMAILS/DOCUMENTS/ENDPOINTS and for your ACCESS to Microsoft products (meaning AD, even if you are a Apple house)
The bottom line is that for ensuring you have the best security you want all or some of those security features:
URL Link protection;
Attachment protection;
Identity and impersonation protection;
Threat Intelligence;
Alert for suspicious logins or activities;
Logs and archiving;
Advanced search and discovery;
DLP
Digital Right Management;
Encryption;
MDM (phones and laptops);
GPO;
Etc.
>>[READ MORE]
 New Download section with Presentations
New Download section with Presentations
A new section has been added to the Download page where you can now find a link to all the public presentations ELYSIUMSECURITY has been giving.
Those presentations cover a wide range of Cyber Security topics and we hope you find them useful.
They are classified as public and you are welcome to re-use them or part of their content, we just ask if you could please reference the source of this material if you do so.
>>[READ MORE]
 FREE Cyber Security Event - 3rd Episode!
FREE Cyber Security Event - 3rd Episode!
Special guest announced for the next MU.SCL event!
Dr Kaleem Usmani from CERT MU will be presenting on Incident Handling.
You can register now HERE !
This FREE to attend meeting will take place on the Thursday 26th of April 2018, from 6pm to 8pm, at the Flying Dodo Brewing Company in Bagatelle, Mauritius.
We are working on a streaming option for those of you who cannot physically attend.
The first talk will present how information shared on social media platforms can easily be obtained and used against you. We will also take a look at recent world events and how this data can be aggregated and why this is dangerous.
The second talk will discuss incident handling in t...
>>[READ MORE]
 MU.SCL - Second Meeting for the Mauritius Cyber Security Club
MU.SCL - Second Meeting for the Mauritius Cyber Security Club
Following the success of last month event, ELYSIUMSECURITY is happy to confirm the second meeting for the Mauritius Cyber Security Club: MU.SCL
This FREE to attend meeting will take place at the Flying Dodo Brewing Company in Bagatelle.
In this second edition, the following two talks will be presented:
The first talk will provide a high level overview of important Cyber Security regulations, standards and best practices relevant to most industries nowadays. At the end of the presentation, attendees should be able to take away key information and follow-up with any questions/worries/debate they may have on the subject.
The second talk will be more technical and focus on how everyone can install an Intrusion Detection System in their home using Open Source software. This talk will hig...
>>[READ MORE]
 MU.SCL - The Birth of a Cyber Security Club in Mauritius
MU.SCL - The Birth of a Cyber Security Club in Mauritius
ElysiumSecurity is proud to announce the creation of a Cyber Security Club in Mauritius: MU.SCLE
This Club has been created to help Mauritian IT Professionals to share information and learn about Cyber Security through an Open Platform and the creation of a Cyber Security Community.
It is a free monthly event open to everyone , usually two talks of 45 minutes each with a mix of technical and non technical talks. Attendees will be able to ask questions, learn and apply practical knowledge as well as do some professional networking.
The first event will take place on the 15th of February 2018, at 18:00 at the Flying Dodo in Bagatelle.
Please REGISTER HERE so we can have an idea on how many people to expect.
We hope to see you there, for what should be a fun, friendly and casual event whe...
>>[READ MORE]
 RSS Feeds
RSS Feeds